Why 2FA isn't enough: zero-trust approach to document security
Why 2FA isn't enough: zero-trust approach to document security.
Two-factor authentication (2FA) protects 2.5 billion accounts worldwide. Yet in 2024 alone, over 100 million accounts with 2FA enabled were still compromised.
Here's why: 2FA stops casual attacks, but it's built on a flawed assumption—that your second factor is actually secure.
Two-factor authentication (2FA) gives you a necessary defense layer. You type your password, get a code, enter it, and feel secure. But this safety feeling often misleads you.
2FA is better than nothing, but it’s not enough on its own. If your phone is stolen, if your SIM card is hijacked, or if you approve one login request too many, someone else can still walk into your accounts.
And if you lose your phone completely, you might be locked out of your own digital life for days or even permanently.
Am I protected when 2FA fails?
Not really.
2FA lowers risk but doesn’t eliminate it. Attackers can use phishing kits to steal both your password and code at the same time, or swap your SIM card so your text messages go to their device. If your phone is stolen and not properly locked, your second factor quickly becomes their first.
Speaking of which, the Identity Theft Resource Center reports that account takeover attacks are a huge threat. While criminals often use stolen credentials, losing or having your 2FA device stolen gives them a direct way to bypass your security.
And when the failure isn’t an attacker but bad luck, like losing your phone, you face another problem. Recovery processes are often slow, require ID verification, or in some cases never succeed. In other words, your security system can easily become your biggest obstacle.
Could this happen to me?
Ask yourself one thing: If I lost my phone tomorrow, could someone get into my accounts within minutes?
If your answer isn’t a confident “no,” then you’re not protected.
How many people actually use 2FA?
Not nearly as many as you’d expect.
Back in 2018, Google software engineer Grzegorz Milka revealed at Usenix’s Enigma conference that less than 10% of active Google accounts have 2FA enabled at all. Awareness has grown since then, but adoption remains low.
And among those who use 2FA, many still rely on SMS codes, the least secure method, simply because it's easier. SMS can be intercepted through SIM swaps or rerouted by carriers. Google’s own research found that over 10% of users had trouble entering SMS codes correctly. A method that is both insecure and unreliable is hardly a solution.
So, even if you’re using 2FA and a password manager, you’re ahead of most people. But being ahead doesn’t mean being safe.
Where does 2FA actually sit in the security food chain?
Let's imagine personal data protection as a food chain in the ocean.
The creatures in this food chain are your levels of defense, and the threats are what they consume. The stronger your defense, the bigger and more powerful the creature, and the higher up the food chain you sit.
Plankton - Just a password. The weakest defense. Easy prey.
Minnow - Password plus 2FA. Stronger, but still vulnerable to bigger predators like SIM swaps or stolen phones.
Trout - Password + 2FA + offline backup codes + a password manager. More resilient, but still fragmented.
Shark - All of the above plus tools that avoid tracking or storing your data. A harder target, but not invincible.
Kraken - The ultimate predator. A zero-trust model where data is encrypted on your device before it leaves. Even the provider can’t read it. A breach gives attackers nothing but scrambled noise.
Most people believe they’re sharks. In reality, they’re minnows pretending to be bigger than they are.
How do attackers bypass 2FA?
There are phishing kits that capture your password and the 2FA code you enter in real time. SIM swap attacks let criminals redirect your text messages, including your login codes, to their own device. Malware can read authenticator app codes straight off your phone's screen.
Back in 2022, Uber suffered a breach after attackers spammed a contractor with push-based 2FA requests until the person finally approved one just to make the notifications stop.
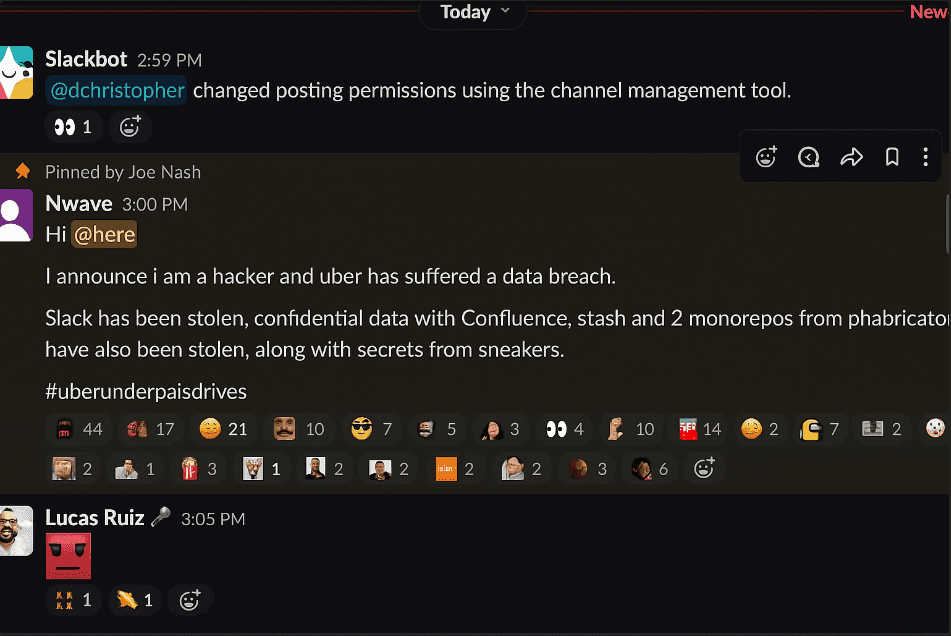
The hacker's message, posted in Uber's Slack channel, announcing the breach. Source: X
That's what we call "MFA fatigue" and they're so common these days that even security researchers have stopped calling them "advanced" attacks. They're just attacks.
Zero-trust philosophy: Becoming the kraken
You’ve seen where 2FA sits in the security food chain: somewhere between a minnow and a trout. To rise above that, you don’t need more codes, backup devices, or extra hoops to jump through. You need a different way of thinking about security altogether.
That way is called zero-trust.
Zero-trust works this rule: never trust, always verify.
It assumes threats can come from anywhere - inside or outside your network, your device, even your own accounts. Instead of trusting the user after one login, every request is checked again and again.
When applied to personal data, zero-trust means:
Absolute control: You alone hold the keys to your information.
Privacy by design: Even your provider can’t see your files.
This approach works because it eliminates single points of failure. It doesn't rely on one factor (like your 2FA code). It assumes all factors are vulnerable and keeps attackers out even if your codes are intercepted or your phone is stolen.
This need for true security is the first reason we built MyVault.
How does MyVault apply zero-trust?
Traditional cloud storage gives you space. MyVault gives you security and answers. We built it because we saw the flaw: space without control just leaves you with digital clutter. You don’t need more folders. You need a system that works for you.
MyVault encrypts your files on your device before they leave your control. That means the servers holding your data only ever see scrambled noise. Even if someone breaks in, they steal gibberish, not information. Only you can unlock it.
But MyVault doesn’t just store documents, it organizes them into meaning. Your receipts link to warranties, warranties to insurance, insurance to assets. You stop hunting and start asking.
Ask natural questions and get real answers:
When does my car registration expire?
Which subscriptions charged me last month?
What insurance covers my camera equipment?
Where’s my warranty for the dishwasher?
MyVault finds files, delivers the right ones in context, with proof attached.
Why does privacy matter more than convenience?
Convenience without privacy is a trap. The more you spread your information across email, drives, and cloud services, the more exposed you are. Hackers know this, which is why large storage providers are prime targets.
Breaches like “Mother of All Breaches,” which exposed billions of records, show what happens when millions of accounts are stored in the same vault.
With MyVault, there is no central vault that can be mined. Every document is locked under your keys alone. We don’t scan your files to target you with ads. We don’t profile your behavior. We don’t sell your data. Your vault is yours.
Why now?
Because digital chaos is only getting worse. More subscriptions. More accounts. More logins. More documents scattered across services. Every year you delay is another year your data is exposed and your family is unprepared.
Right now, MyVault is in limited beta. That means you can shape how it grows.
Will you stay a minnow, or become the kraken?
You’ve seen why 2FA is not enough. You’ve seen how attackers bypass it and how fragile your own phone can be as a “second factor.” You’ve also seen zero-trust security with full privacy and control.
MyVault ensures that level of protection and makes your digital life not only safer but smarter. Instead of clutter and chaos, you get order and answers.
Stay vulnerable with a false sense of safety, or take real control with a system built for the threats of today.
The choice is yours.
Related posts
Feb 3, 2026
Household systems that pay for themselves in hours
Mental load means remembering when car insurance renews, tracking which child needs new shoes, knowing the fridge filter expires next month. Every household runs on hundreds of small details that someone must hold in memory.

Sead Fadilpasic
Jan 27, 2026
The Habsburg effect: why your data just got more valuable
The European Habsburgs built an empire through strategic marriages, consolidating power by keeping bloodlines strictly within the family. Something similar is happening with AI right now.

Markos Symeonides
Jan 21, 2026
The superuser problem: why AI agents are 2026's “biggest insider threat”
The primary security issue with AI agents is their access.

Markos Symeonides




